Steps to configure P2S VPN is mentioned below and you can follow the steps to configure your site to point VPN.
There are mainly four categories of VPN provided by the Azure for the time. Those are.
1. Point-to-Site (VPN over IKEv2 or SSTP)
2. Site-to-Site and Multi-Site (IPsec/IKE VPN tunnel)
–> Site to Site and Multi Site VPN service
3. VNet-to-VNet connections (IPsec/IKE VPN tunnel)
4. Site-to-Site and ExpressRoute coexisting connections
If you want more information or the connectivity information, you can click on the links and find them.
If you want more information about the Azure VPN pricing, then click on this Link
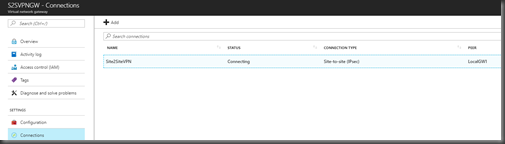
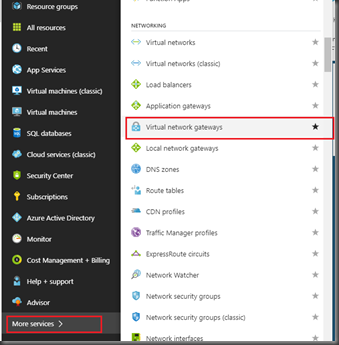
To start the S2S configuration, you need to go into
Virtual network gateways > Select the Gateway that you have created earlier
Then select Point-To-Site Configuration and click configure now.
If you have not created your Virtual Network Gateway, you can follow my blog post which is describe about that.

Then give an address pool which you want to use and select the tunnel types below.
Select SSTP protocol.
SSTP(Secure Socket Tunneling Protocol) is a new form of VPN tunnel with features that allow traffic to pass through firewalls that block PPTP and L2TP/IPsec traffic. SSTP provides a mechanism to encapsulate PPP traffic over the SSL channel of the HTTPS protocol. The use of PPP allows support for strong authentication methods such as EAP-TLS. The use of HTTPS means traffic will flow through TCP port 443, a port commonly used for Web access. Secure Sockets Layer (SSL) provides transport-level security with enhanced key negotiation, encryption, and integrity checking.

I have selected the Azure Certificate as the authentication type. And to use the certificate you need to Generate a Root and a Client certificate.
Steps to create the certificate can be found here.
Once you copy and paste the Certificate you will be able to save the new configuration.
Next the Download VPN client tab will be active and you will able to download the VPN client from that.

You can generate the client Certificate by using the below command,
makecert.exe -n "CN=AzureClientVPNCert" -pe -sky exchange -m 96 -ss My -in "AzureClientVPNCert" -is my -a sha1
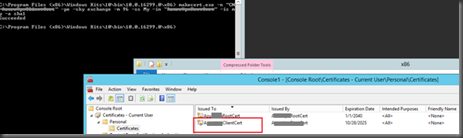
Then import the certificate into the Personal Certificate folder and install the VPN client on the PC which you want to use this VPN.
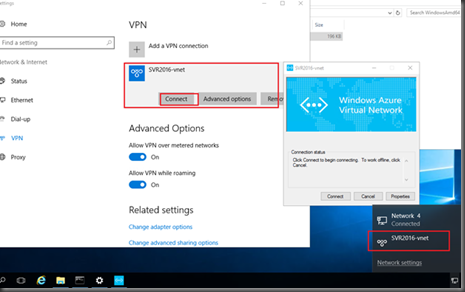
If you have imported the Client Certificate correctly, then you will be able to connect your client VPN without any issues.

You can download the generated Certificate from https://gallery.technet.microsoft.com/Azure-Point-to-VPN-3613dbeb location.
This will help you to do the initial testing.